This release consists of the following:
- 64-bit CryptOne Crypter and loader components
- MjrMnr implant (CT named malware)
- GuLoader VBScript loader and Powershell downloader
- Akira ransomware “The Return” variant
- SLNYA ransomware
- Abyss Locker ransomware
- HellDown ransomware
- Razr ransomware
- Interlock ransomware
- Smert Locker
- VeilShell malware
- Cake (CT named malware) components: Dropper, Loader, Injector
- JPHP malware (named for entity folder or project names in namespace PHB files):
- JLoader downloader: 371eb4c02b59c0cf677c8038444936b2
- Thunder downloader: daedfce55468631ab0cedc49b0d9da57
- axelp downloader: 2c609c2d39e0f24cb3382277784cc50b
- HijackLoader variant which uses RGB+XOR decoding methodology
- awesome clipper (GoLang and C++ variants)
- l33tninja downloader (CT named malware)
- Absolute CryptoMiner (CT named malware)
- CoinSurf installer and client (CT named malware)
- ACR Stealer support for variant which uses cityhash for API resolution instead of FNV1a
MjrMnr Implant
During investigation of the sample referenced in a post by X user @naumovax, we identified that the provided hash is for a 64-bit variant of CryptOne. However, attempts to identify the payload as a known malware family proved unfruitful, and we have named the malware MjrMnr based upon unique strings within the binary used to capture compromised system information.
While some strings are in plaintext, MjrMnr XOR encodes the c2 socket address and file extensions using an 8-byte key. The implant then collects compromised system, including the operating system major, minor, and build numbers; the current username; and if the account is running using elevated privileges. After the information is sent to the server, the implant is capable of downloading a .bat, .cmd, or .exe file for execution.
During research we found 10 unique MjrMnr samples, all configured to communicate with either 64.95.13[.]143:1120, 91.92.250[.]213:1050, or 94.156.68[.]124:1122.
- CryptOne + MjrMnr: 54a1448df6e33d7032232dd1d896bc68
Cake Malware
While conducting research we identified a multi-stage dropper we are calling “Cake” based on the name of the variable storing a payload in most of the identified samples.
The primary Cake component is a dropper written in PowerShell which contains three (3) loader components written using VBScript, Batch, and PowerShell. The VBScript is responsible for running the Batch script, which runs the PowerShell script, which loads an injection component and embedded payload.
The VBScript is then installed on the compromised system as a scheduled task.
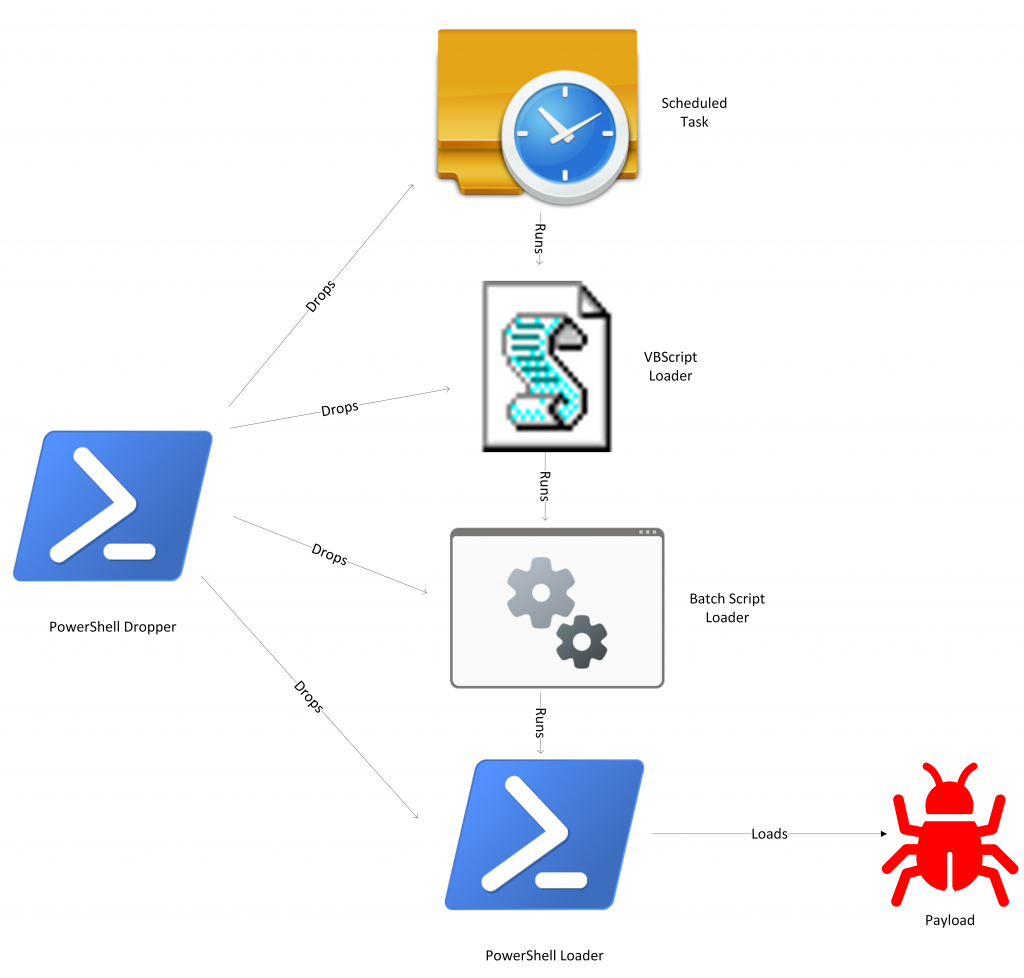
Cake Installation
Some Cake droppers will call out to Telegram to indicate success, sending a message which includes the public IP address of the compromised system.
The PowerShell loader contains a hex-encoded and obfuscated payload and injection component. Before hex-decoding, each binary string is split by a delimiter, typically “_”.
After decoding, the injection component is injected into a newly created process, typically C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe with the payload binary as an argument for subsequent execution.
In our research we identified 40 Cake dropper samples whose payloads included AsyncRAT Stealer, QuasarRAT Stealer, and XWorm RAT.
- Cake + AsyncRAT: bedf882443aea1bf50e30409bea0ba92
- Cake + QuasarRAT: ac7518bd1594218c377c218fb5f7a439
- Cake + XWorm: 0a0c62ce8d5c5b894a1e4ebd38e40405
HijackLoader RGB+XOR
While researching the HijackLoader (aka GhostPulse) update, which uses steganography to decrypt a payload, we identified ~120 loader components (contains the payload within its binary) and ~50 downloader components (downloads the payload).
In addition to Lumma Stealer, as reported by Elastic Security, we extracted numerous payloads from the identified loader components, including ACR Stealer, Amadey Stealer, BSR Crypter, Racoon Stealer, Remcos, Rhadamanthys, SectopRAT, StealC, and new malware we are calling Absolute CryptoMiner, awesome Clipper, CoinSurf, and l33tninja Downloader.
Absolute CryptoMiner
Absolute CryptoMiner consists of two (2) components, a .NET installer and an XMRig CryptoMiner. Its name is derived from the RFC2898 password observed in samples – “ABSOLUTELY”. The CryptoMiner may be AES-CBC encrypted in the installer’s .NET resources or alternatively downloaded and then dropped to disk.
To run the XMRig CryptoMiner, Absolute will Base64 decode and AES-CBC decrypt the command line configuration. The AES key to decrypt the configuration is derived using the SHA256 hash of a hard-coded string and the IV is null. It should be noted that the AES key and IV used to decrypt the component from the resources is derived using RFC2898 (PBKDF2).
For installation, the Absolute installer will copy itself to a hard-coded destination and is capable of creating a scheduled task, although this method was not referenced in the observed sample.
- HijackLoader + Absolute: e07f55ea76d0b6eeb2afde67e2c19fde
awesome Clipper
From HijackLoader we initially observed two GoLang versions of awesome Clipper (named from the GoLang project path “awesomeProject”), which use two different string decryption methods. One uses XOR and the other uses AES-CFB. By pivoting on the observed XOR key, we found a variant on VirusTotal written using C++ which is configured with the same CryptoCurrency addresses an regex patterns.
awesome Clipper is either configured with a c2 address or dead-drop resolver URLs, observed as steam community profile links. The usage of dead-drop resolution was only observed in the AES-CFB variant, and the socket address is AES-CFB encrypted and hex-encoded in a comment on the profile.
- HijackLoader + awesome (XOR): 8c80b75b589ea7dea1707a03148571b8
- HijackLoader + awesome (AES-CFB): b3251fbdc10f347197a02b11f857d4d3
- awesome C++ (XOR): 3a040e06d5ced4255e0060bd6f93ff75
CoinSurf
CoinSurf consists of an installation and Client component, where the Client component communicates with https[:]coinsurf[.]com/api/v4/client/settings for runtime settings. The CoinSurf website advertises itself as “a passive income platform where members can […] share unused internet bandwidth.”
The installation component is configured with an API key for running the Client, installs itself in the registry, and will periodically check for updates.
- HijackLoader + CoinSurf: ed8d6c66dec694933a070bb9ba976f4d
l33tninja Downloader
l33tninja is a downloader named for the username in its PDB path, which will attempt to download a ZIP archive, and download and execute a PE executable.
- HijackLoader + l33tninja: fad3eabc4a5eafafc6295ce3e0454881
