
What is ACCE?
ACCE is a framework that runs targeted modules to automatically deobfuscate layers of embedded malware components and extract configuration data, including valuable Indicators of Compromise (IoCs). This process does not require running or emulating any of the malware, as the entire analysis process is conducted statically by re-implementing the algorithms that the malware uses to unpack its embedded components and access its configuration data.
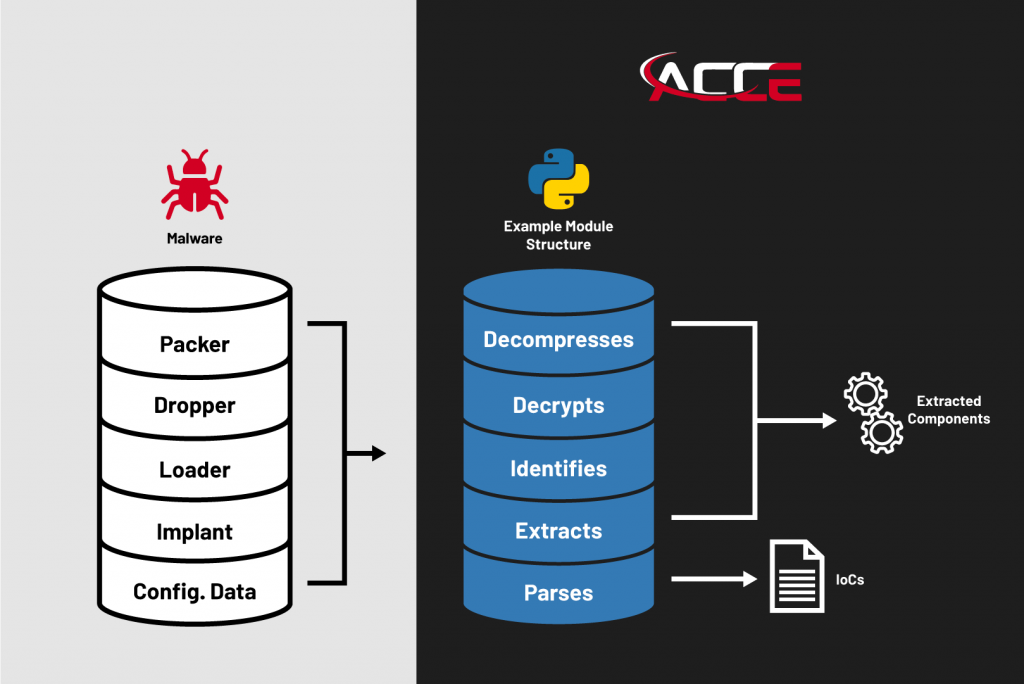
Unlike sandboxes and anti-virus tools, which are designed to provide broad information about all malware, ACCE is a targeted capability that aims to provide more detailed and relevant information tailored for the specific threats that your organization may be interested in understanding better.
What kind of malware do we support?

All malware, regardless of its sophistication, must avoid detection, and thus will inevitably include some form of obfuscation of its embedded components and configuration data to protect itself.
In our experience, the parsers that we create to handle the configuration do not change as frequently as the obfuscation methods employed to protect the outer layers. Therefore, an ACCE analysis module can be easily updated to maintain relevance without recreating it from scratch for every new variant of a malware family. For example, the underlying configuration data structure likely remains unchanged, but the obfuscation algorithms which protect it are likely much more variable, and thus will require updates as those changes are made.
How does ACCE work?
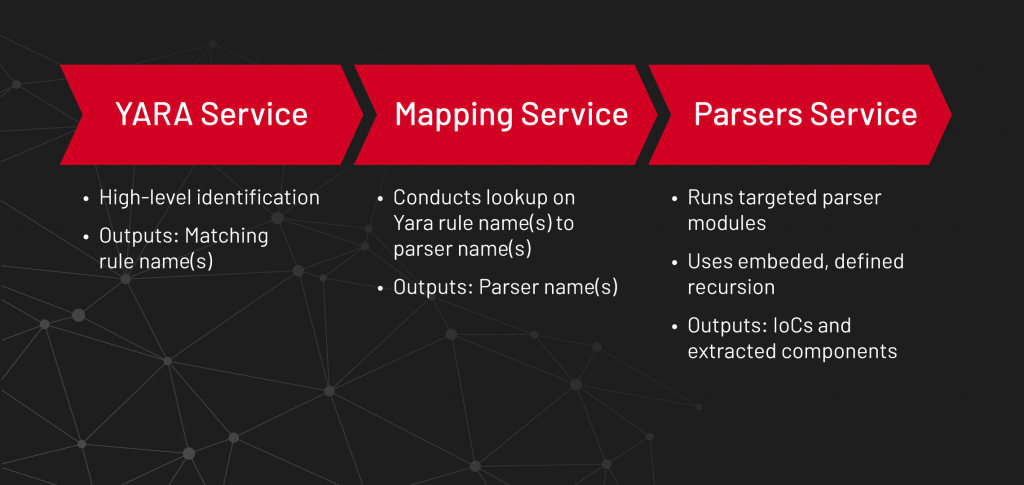
ACCE consists of a series of micro-services, built using Docker containers, which run targeted ACCE modules based upon YARA signatures. These design considerations were not only ideal for automating the ACCE workflow, but also integral for ACCE integration into larger automation platforms, as each micro-service was designed to be substituted and easily scale for various deployment needs.
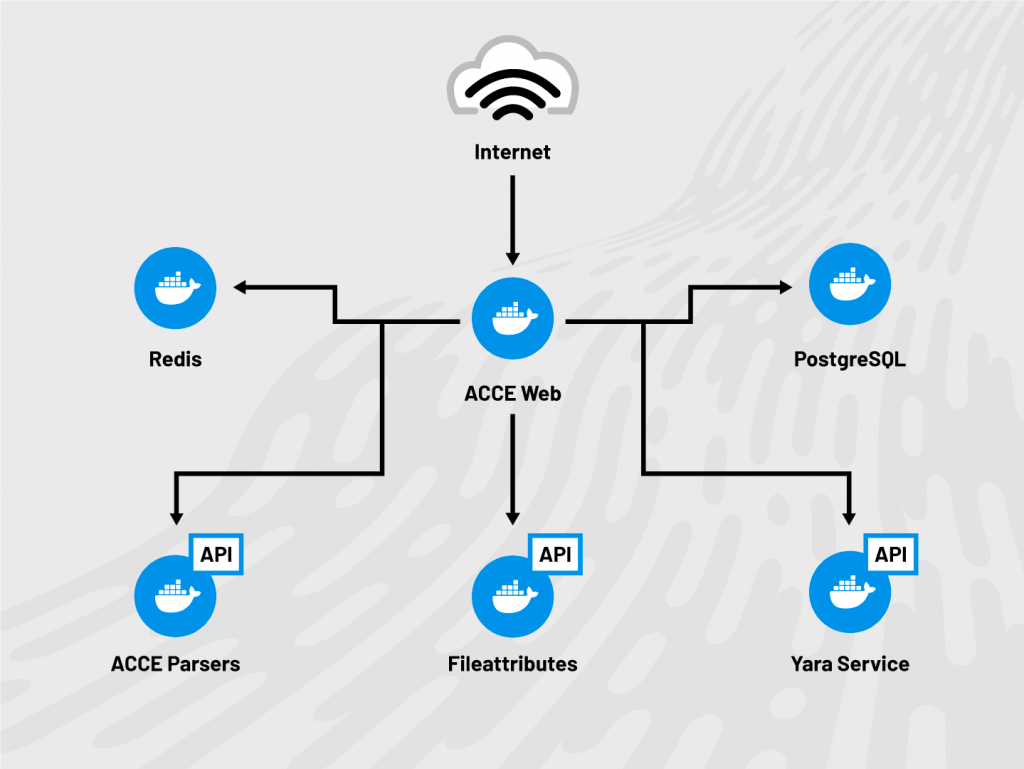
How do ACCE modules get created?
Cipher Tech’s reverse engineering teams are continually expanding and updating their corpus of signatures and tailored ACCE Python modules that automate the identification, decryption, and extraction of embedded components and configuration data. At Cipher Tech, we monitor the latest trends in public reporting and aim to support related malware within our ACCE modules. Additionally, we work with our partners and customers who can nominate new malware families or significantly-changed variants for inclusion within ACCE. Customers also have the ability to add their own ACCE modules to their own internal instances of ACCE.
Who can benefit from using ACCE?
ACCE helps to better scale the reverse engineering process by providing workflows that your engineers can extend upon as they are tasked with understanding the most current threats that face your organization.
ACCE empowers your threat intelligence teams by providing them with the IoCs that they need to identify threats and defend their networks.

How many ACCE modules are created?
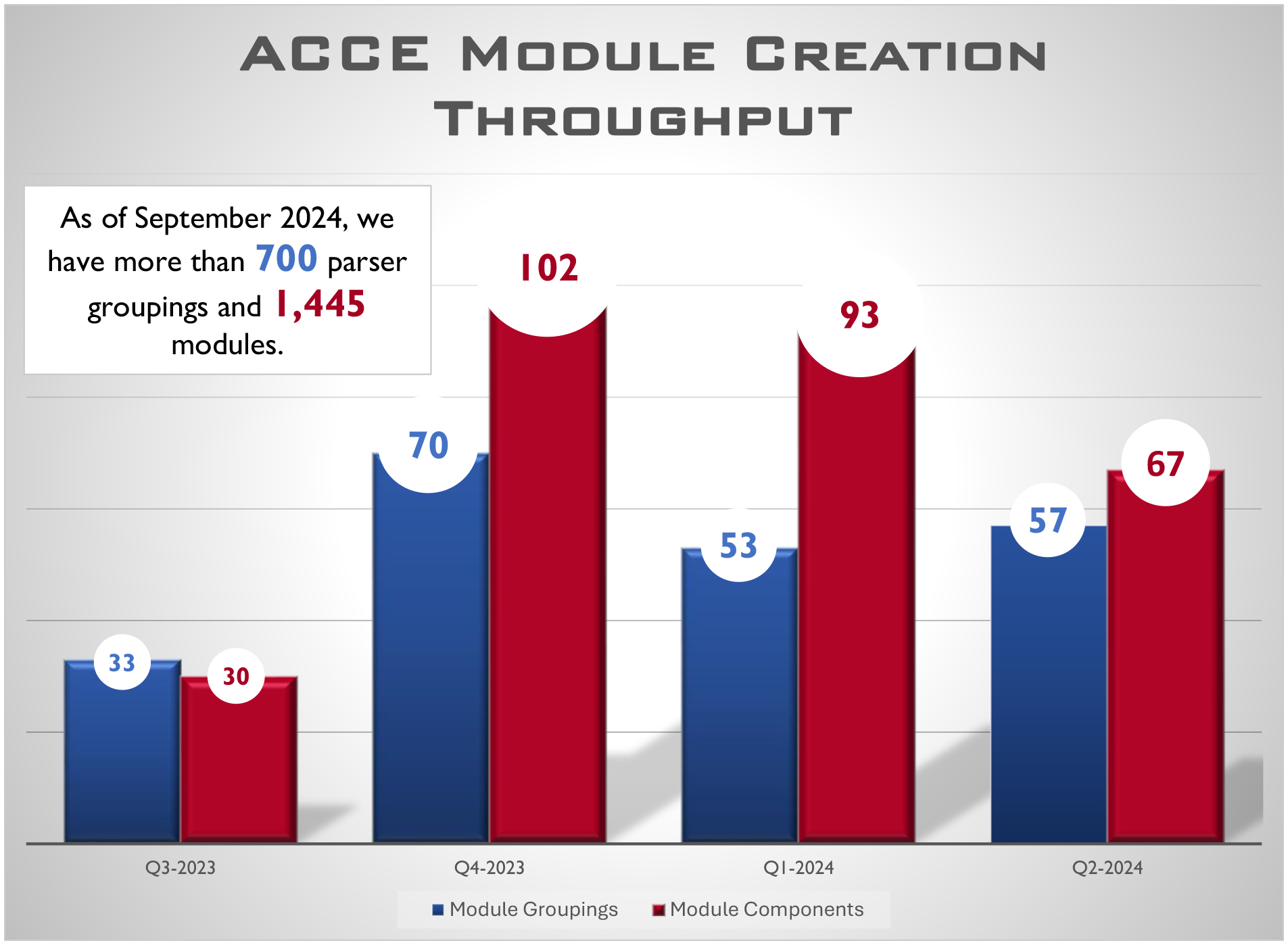
As of September 2024, we have more than 700 module groupings, encompassing malware families, threat actors, and attack vectors. These consist of more than 1,445 module parsers, covering different components of a grouping (droppers, implants, etc.) and their variants supported by more than 900 YARA signatures.
What’s in an ACCE subscription?
- Daily (or as required) updates to ACCE modules and signatures.
- Through a nomination process, we will prioritize adding modules for samples you provide which are not yet supported.
- ACCE modules and supporting libraries/utilities, written in Python, which can be leveraged and extended by your in-house teams. Like ACCE modules, these supporting libraries are also constantly maintained and updated.
- ACCE contains both a lightweight UI and a stand-alone API for integration into your existing automation solutions.
- ACCE can operate entirely online or offline depending on your subscription level.
Using ACCE through the UI
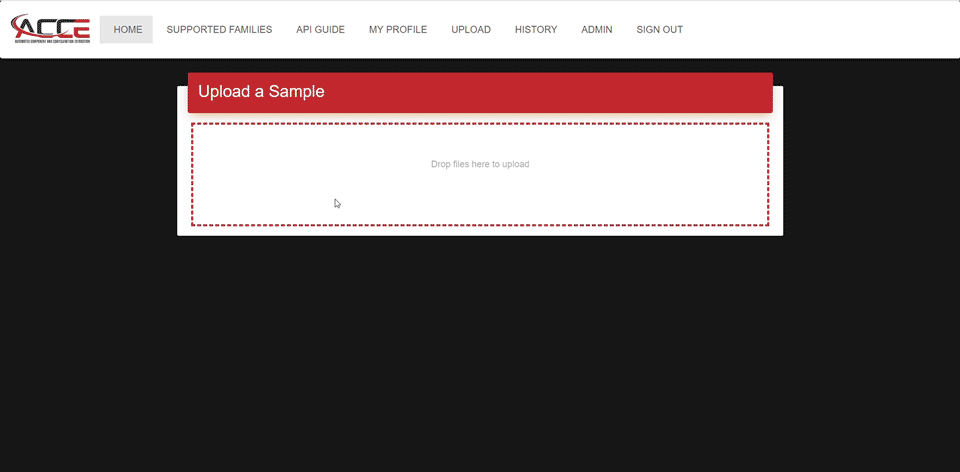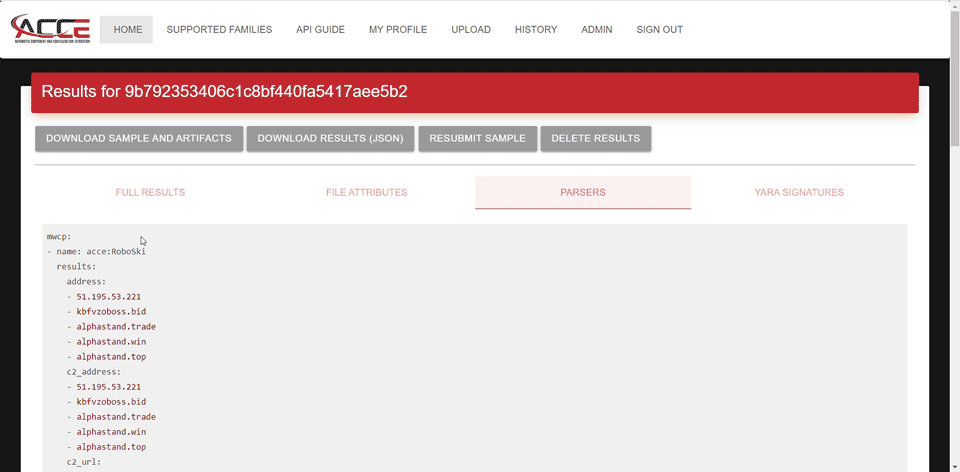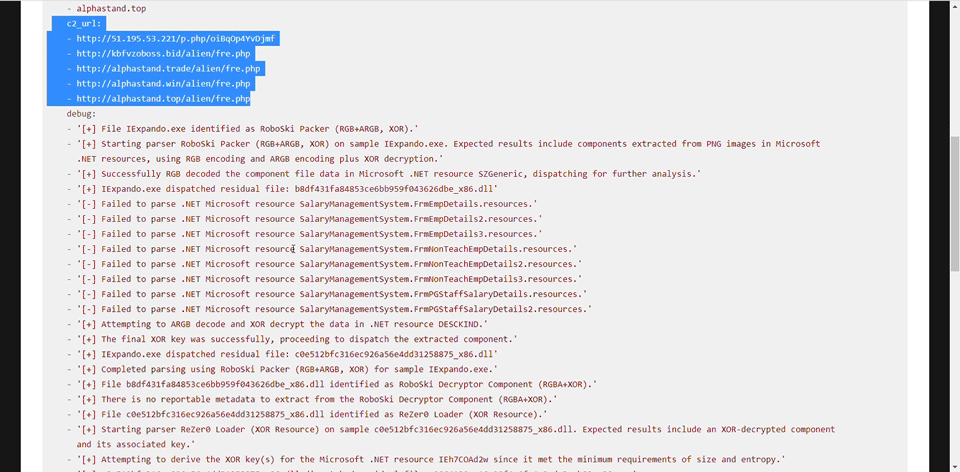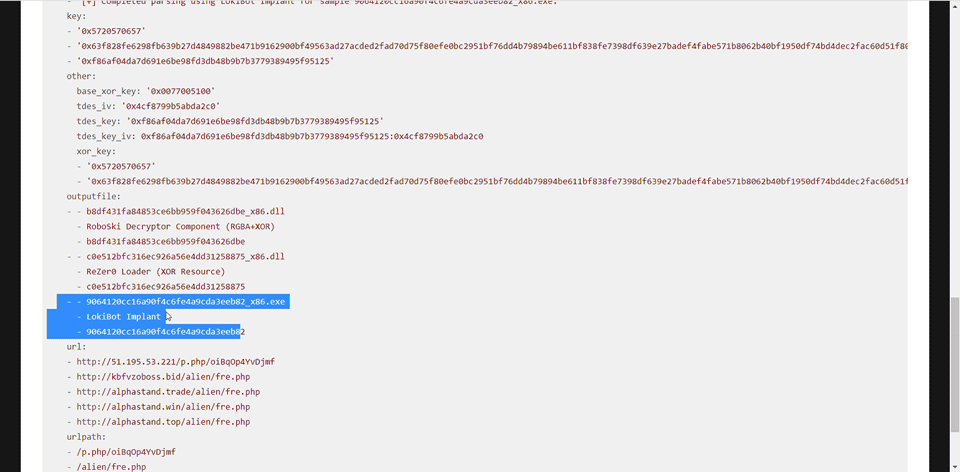
Using ACCE through the API

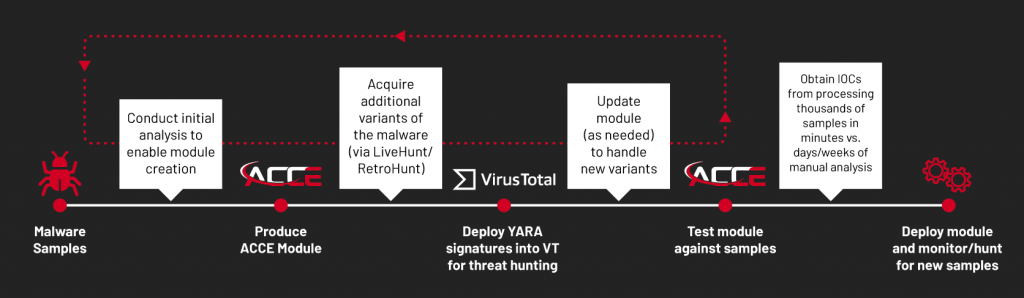
Threat Hunting with ACCE
Tiers of ACCE support
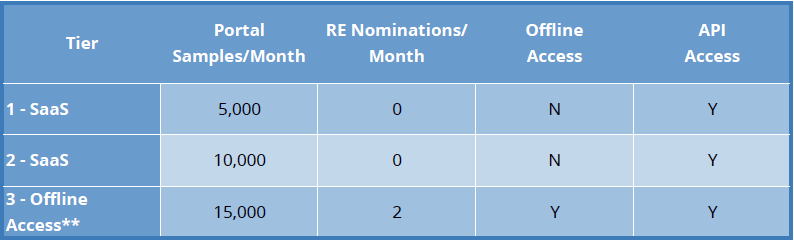
ACCE extensibility (through tier 3 support)
We have designed the ACCE framework in a way that can be used entirely offline, integrated into your existing processing pipelines, or used in our hosted portal.
If you have a reverse engineering team and the offline version of ACCE, those individuals can write custom signatures and/or decryption and extraction modules with ease to further broaden the platform’s capabilities.
What can ACCE do for your team?
ACCE can be a force-multiplier to allow smaller teams to have a broader reach and to enable teams of any size to work more efficiently. ACCE also empowers analysts and network defenders to self-serve by leveraging the automated capabilities to acquire IoCs without necessarily having to involve a reverse engineer.
Anonymity
Cipher Tech is committed to protecting the equities of each customer. As such, ACCE submissions and requests remain anonymous between users.
Contact Information
For a demo, please contact acce@ciphertechsolutions.com.
Public Security Commitments
Please see our security commitments available here.
